I eventually came across a great and simple to use perl script named CryptoNark. This tools was easy to get running on my Backtrack R3 box I have hanging around my desk. I did have to install a few dependencies first to get it running. I had to run the following 3 commands to install the dependencies.
- cpan Modern::Perl
- Cpan Tie::Hash::Indexed
- Cpan Mozilla::CA
After completing those commands I was able to run the script with the following syntax:
./cnark.pl -h "Hostname/IP" -p 443 --insecure
The --insecure is used to ignore self-signed certs. The result will look similar to this.
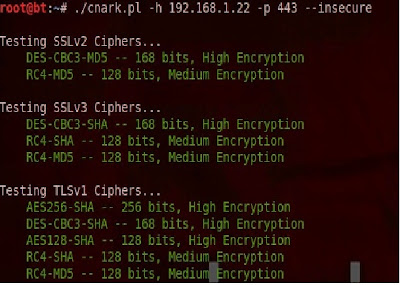
Now that we have confirmed that SSLv2 is alive and kicking on our server we need to disable it. I found the following page on an MSDN blog that did the trick for me. It is a simple registry change:
Open the registry and find:
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server
I believe I may have had to create the Server key.
Then add a new REG_DWORD with a name of DisabledByDefault. Give it a value of 0x1 to disable SSLv2 by default.
Once this was done I tried to just reset IIS to see if the change would be effective without a reboot but it did not work. After rebooting the system I ran the cnark.pl script again and the result looked like:
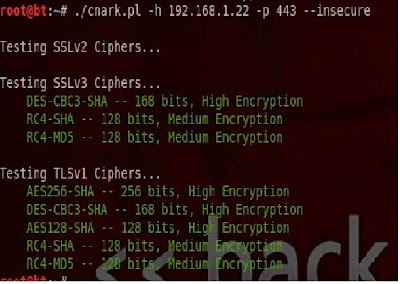
And there you have it, SSLv2 is disabled. This would definitely be something that could easily be added to a server build script or added to a base image so you don't have to do this every time.
Adios!!
No comments:
Post a Comment