I am now done with studying for the CEH (passed exam last week) so I'm looking for my next endeavor. I'm currently taking an Offensive Security (penetration testing) course from Dakota State so I'm still keeping those skills somewhat fresh with the course.
I've decided to go back to Python and dig into it more. I read Think Python over the summer but didn't really put much effort into it. I basically just read it and did the examples in the book, didn't really do any of the exercises or anything like that. This time I am going to try to do the exercises and maybe post them on here just so that will motivate me to actually do them. I'm currently using the book at http://learnpythonthehardway.org/ right now but will also use Learning Python 5th Ed., Programming Python 4th Ed., Python Cookbook 3rd Ed., Violent Python, and Gray Hat Python. I really want to concentrate on how I can use Python to learn more about Pen Testing, Reverse Engineering, and Malware Analysis.
Hopefully I will be posting back soon with some answers to exercises as I'm diving into Python.
Defend Your Systems
A blog on my journey learning about Penetration Testing, Forensics, and Malware Analysis.
Sunday, September 8, 2013
Sunday, August 11, 2013
Building My Penetration Testing Lab
One of the key ingredients to learning the hacking techniques needed for penetration testing is having a decent lab to practice in. For the past year I've basically just been using VMWare Player on my PC and would run a VM running Kali Linux and one running Metasploitable. This was enough to play around with some tools while reading some of the books but I knew at some point I would want to have a little more complex lab to play around in.
My PC up until a few weeks ago was a 3-core box with 8 GB of RAM and about 300 GB of disk space. This is the main PC that my family uses so a lot of that disk space was allocated and it left me with a little space for VMs, maybe 2-4 at a time. 8GB of RAM was also a limiting factor when running VMs. I had contemplated building a server to run VMWare ESXi or Hyper-V on that would house my whole lab but I really haven't been able to justify the cost. What I ended up doing was just buying 16GB of RAM and an additional 1TB hard drive to get my machine in a state that it could handle running 6-8 VMs at a time.
Here is a picture of what my lab looks like right now in VMWare Player.
A couple of things I wanted to have in my lab were:
1) Internet Access but segregated from my home network
2) 2 separate subnets with a firewall in between
3) a system that I could watch the traffic on with wireshark and snort
4) a mixture of vulnerable VMs to practice on
I created 2 separate networks within VMWare Player, one named secure and one named unsecure. I have 2 "attacking" machines on the unsecure network, Kali Linux and Windows 7. On the secure network I have a Windows 2012 domain controller mainly to offer DNS and DHCP services for that subnet. I also will probably add a client to the domain and just sniff that traffic to see what it looks like when the client authenticates among other things. I also have an older Ubuntu 9 server, Metasploitable, UltimateLAMP, and Win XP w/ SP2 that I can bang around on and practice some of the techniques I am learning.
On the unsecure network, I have a m0n0wall distribution as the gateway for Internet access. It is just a basic default setup and nothing special. On the box named "Snort" that connects the 2 networks together, I just have IP forwarding turned on and some basic firewall rules that allow traffic between the two networks. The 3 rules I had to add on that box are:
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
iptables -A FORWARD -i eth1 -o eth0 -j ACCEPT
iptables -A FORWARD -i eth0 -o eth1 -j ACCEPT
I had troubles getting the traffic between the two networks to work initially with the basic ACCEPT rules that are on iptables by default and adding these are the only way I could get it to work. I actually think just using the MASQUERADE rule is sufficient enough but I added the last 2 just in case. I intend to play around with iptables more at some point during my practicing to see how firewall rules will affect some traffic and see if there are ways to bypass the firewall. I have the box named "Snort" because when I originally created this VM it was going to just run Snort to watch traffic on the private network while I'm testing out techniques. I still haven't actually gotten around to setting up snort on the box but that is on my list of "To Dos".
Static routes are also needed on the Kali and WinPen boxes to the 192.168.10.0/24 that tell them to send traffic destined for that network to the 192.168.20.5 interface on "Snort". Otherwise, they will try to send the traffic out the 192.168.20.1 interface on "m0n0wall".
This is just a start to my lab, hopefully I will add some more vulnerable systems to the secure network. If you have any suggestions on good vulnerable systems to test with please let me know.
Monday, June 24, 2013
Quick Update
Just wanted to post a quick update since it has been quite a while since I've posted anything. The family finally made it through a hectic schedule the past few months and I will be working a more normal 9-5 schedule now. Hopefully I will be able to put some decent blog posts together soon.
I had blogged about possibly starting school at Western Governor's University but I have decided not to go that route. I came across the Information Assurance program at Dakota State and after checking out its offerings and classes I really like what I saw. I have been accepted to start the Information Assurance - Ethical Hacking Graduate Certificate this Fall. I'm really excited because it is in line with what I want to learn. If everything goes well with the Graduate Certificate then I plan to continue on with the Masters of Science in Information Assurance and Computer Security (MSIA) degree. It will be a long road but I think it will be well worth it.
My reading lately has been mostly around scripting. I'm in the middle of reading Learn Windows Powershell 3 in a Month of Lunches and recently just finished Think Python. I intend to dig deeper into both of these scripting languages, both are extremely powerful.
Hope everyone has a great summer.....
I had blogged about possibly starting school at Western Governor's University but I have decided not to go that route. I came across the Information Assurance program at Dakota State and after checking out its offerings and classes I really like what I saw. I have been accepted to start the Information Assurance - Ethical Hacking Graduate Certificate this Fall. I'm really excited because it is in line with what I want to learn. If everything goes well with the Graduate Certificate then I plan to continue on with the Masters of Science in Information Assurance and Computer Security (MSIA) degree. It will be a long road but I think it will be well worth it.
My reading lately has been mostly around scripting. I'm in the middle of reading Learn Windows Powershell 3 in a Month of Lunches and recently just finished Think Python. I intend to dig deeper into both of these scripting languages, both are extremely powerful.
Hope everyone has a great summer.....
Friday, February 8, 2013
Use Powershell to Find Adobe Flash Version
Hello all!! Wanted to put up a post about a quick and dirty script that I wrote to check the Flash version on machines in a domain.
This can be run on all computers in the domain or you could specify the OU to search. This script will output to a tab delimited file named get_flash_version_output.txt by default but you can specify your own output file if desired. Here's the code:
Generic execution which will iterate through your whole domain and output to get_flash_version_output.txt
PS C:\> .\get_flash_version.ps1
Execution specifying a specific searchbase within Active Directory
PS C:\> .\get_flash_version.ps1 -searchbase "dc=Your,dc=Domain"
Put it all together -> use searchbase, verbose output, and write to a different output file
PS C:\> .\get_flash_version.ps1 -searchbase "dc=Your,dc=Domain" -verbose -output test.txt
Another feature I'd like to add is maybe have it grab the current version of Flash from HERE and let you know if you need to upgrade or not.
But that is for another time….
This can be run on all computers in the domain or you could specify the OU to search. This script will output to a tab delimited file named get_flash_version_output.txt by default but you can specify your own output file if desired. Here's the code:
[CmdletBinding()]
param(
$searchbase = $null,
$output = ".\get_flash_version_output.txt"
)
# if the searchbase isn't specified then use the default domain of the user
if($searchbase -eq $null)
{
$searchbase = ([adsi]'').distinguishedName.ToString()
}
#load all computer objects into a variable
$computers = Get-ADComputer -SearchBase $searchbase -Filter * -SearchScope Subtree
#iterate through each computer object
foreach($computer in $computers)
{
$name = $computer.name
# test to be sure you can communicate with the machine, ignoring any errors
if(Test-Connection $name -count 1 -ErrorAction SilentlyContinue)
{
# file that we will be querying for the version
$filename = "\\$name\c$\windows\system32\macromed\flash\flash*.ocx"
# test the path to be sure it exists before trying to check the version
if(Test-Path $filename)
{
$file = get-item $filename
$version = $file.versionInfo.fileversion -replace ",", "."
}
else
{
$version = "Not Installed"
}
write-verbose "$name`t$version"
"$name`t$version" | out-file -append $output
}
else
{
write-verbose "$name`tOffline"
"$name`tOffline" | out-file -Append $output
}
}
Generic execution which will iterate through your whole domain and output to get_flash_version_output.txt
PS C:\> .\get_flash_version.ps1
Execution specifying a specific searchbase within Active Directory
PS C:\> .\get_flash_version.ps1 -searchbase "dc=
Put it all together -> use searchbase, verbose output, and write to a different output file
PS C:\> .\get_flash_version.ps1 -searchbase "dc=
Another feature I'd like to add is maybe have it grab the current version of Flash from HERE and let you know if you need to upgrade or not.
But that is for another time….
Monday, February 4, 2013
Disable SSLv2 on Windows 2008
Recently I was tasked with disabling SSLv2 on a few Windows 2008 servers that are Internet-facing due to SSLv2 vulnerabilities. I have performed this change in the past but did not really use any tool to confirm my change worked at the time. This time I decided to poke around the Internet and see if there were any tools that I could run before and after the change to ensure SSLv2 wasn't "listening" anymore.
I eventually came across a great and simple to use perl script named CryptoNark. This tools was easy to get running on my Backtrack R3 box I have hanging around my desk. I did have to install a few dependencies first to get it running. I had to run the following 3 commands to install the dependencies.
After completing those commands I was able to run the script with the following syntax:
./cnark.pl -h "Hostname/IP" -p 443 --insecure
The --insecure is used to ignore self-signed certs. The result will look similar to this.
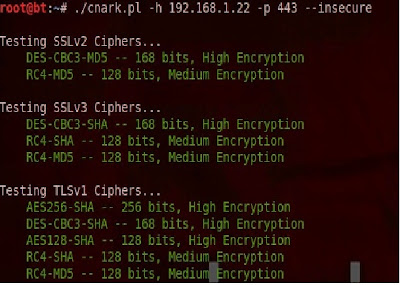
Now that we have confirmed that SSLv2 is alive and kicking on our server we need to disable it. I found the following page on an MSDN blog that did the trick for me. It is a simple registry change:
Open the registry and find:
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server
I believe I may have had to create the Server key.
Then add a new REG_DWORD with a name of DisabledByDefault. Give it a value of 0x1 to disable SSLv2 by default.
Once this was done I tried to just reset IIS to see if the change would be effective without a reboot but it did not work. After rebooting the system I ran the cnark.pl script again and the result looked like:
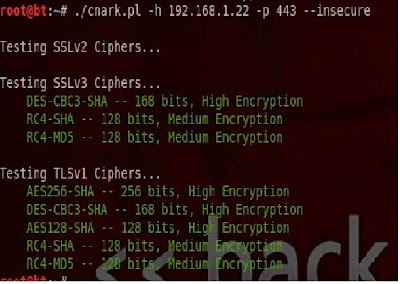
And there you have it, SSLv2 is disabled. This would definitely be something that could easily be added to a server build script or added to a base image so you don't have to do this every time.
Adios!!
I eventually came across a great and simple to use perl script named CryptoNark. This tools was easy to get running on my Backtrack R3 box I have hanging around my desk. I did have to install a few dependencies first to get it running. I had to run the following 3 commands to install the dependencies.
- cpan Modern::Perl
- Cpan Tie::Hash::Indexed
- Cpan Mozilla::CA
After completing those commands I was able to run the script with the following syntax:
./cnark.pl -h "Hostname/IP" -p 443 --insecure
The --insecure is used to ignore self-signed certs. The result will look similar to this.

Now that we have confirmed that SSLv2 is alive and kicking on our server we need to disable it. I found the following page on an MSDN blog that did the trick for me. It is a simple registry change:
Open the registry and find:
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server
I believe I may have had to create the Server key.
Then add a new REG_DWORD with a name of DisabledByDefault. Give it a value of 0x1 to disable SSLv2 by default.
Once this was done I tried to just reset IIS to see if the change would be effective without a reboot but it did not work. After rebooting the system I ran the cnark.pl script again and the result looked like:

And there you have it, SSLv2 is disabled. This would definitely be something that could easily be added to a server build script or added to a base image so you don't have to do this every time.
Adios!!
Saturday, December 29, 2012
Merry Christmas and Happy New Year
It has been quite a while since I have posted anything to this blog. Life has been very busy the past few months. Between an email migration at work and our third child arriving about 10 days ago life has been hectic. I have been able to work on studying for my Security+ certification though. I finished reading CompTIA Security+ SY0-301 Authorized Cert Guide, Deluxe Edition (2nd Edition) and it was a pretty good read. I was scoring around 95% on most of the quizzes at the end of the chapters and the first practice test I took I scored about 82%. Not real thrilled with that score and I definitely have a weakness when it comes to some of the crypto stuff so I will need to concentrate on that more. My experience as a systems admin has definitely helped me when it comes to some of the material. Learning Exchange 2010's Roles Based Access has definitely helped along with other things like deploying SSL certs.
I keep hearing about how good Darril Gibson's CompTIA Security+: Get Certified Get Ahead: SY0-301 Study Guide book so I bought the Kindle version on Amazon for $9.99 and am currently going through it. I'm only in chapter 2 but so far I like his writing style and he gives great examples of certain security concepts. His "Remember This" sections throughout the chapters are great to put into my OneNote notebook for easy reading later. I think it will be a great way to brush up on the material while studying.
I am also reading CompTIA Security+ Rapid Review (Exam SY0-301) on my Motorola Xoom when I don't have time to sit down and read Darril's book and take notes. After I have finished these books and read over my notes a few times I will be using CompTIA Security+ SY0-301 Authorized Practice Questions Exam Cram (3rd Edition) for practice tests and do my final preparations for the test.
Overall I feel pretty confident I can pass this exam and move on to the next step.
I've been really trying to figure out what my next steps are going to be after Security+. After looking at some Pen Testing jobs on some job boards to figure out the tools, certifications, and skills that are listed the most I believe my next step may be doing the C|EH certification. Also, I'm looking at doing the SecurityTube Python and Metasploit certifications. Finally, I really want to go after the OSCP certification but I have a lot to learn before I can even attempt that. This should keep me busy for the next year to 18 months I would think. There is so much to learn and I can't wait to keep trucking along…..
I keep hearing about how good Darril Gibson's CompTIA Security+: Get Certified Get Ahead: SY0-301 Study Guide book so I bought the Kindle version on Amazon for $9.99 and am currently going through it. I'm only in chapter 2 but so far I like his writing style and he gives great examples of certain security concepts. His "Remember This" sections throughout the chapters are great to put into my OneNote notebook for easy reading later. I think it will be a great way to brush up on the material while studying.
I am also reading CompTIA Security+ Rapid Review (Exam SY0-301) on my Motorola Xoom when I don't have time to sit down and read Darril's book and take notes. After I have finished these books and read over my notes a few times I will be using CompTIA Security+ SY0-301 Authorized Practice Questions Exam Cram (3rd Edition) for practice tests and do my final preparations for the test.
Overall I feel pretty confident I can pass this exam and move on to the next step.
I've been really trying to figure out what my next steps are going to be after Security+. After looking at some Pen Testing jobs on some job boards to figure out the tools, certifications, and skills that are listed the most I believe my next step may be doing the C|EH certification. Also, I'm looking at doing the SecurityTube Python and Metasploit certifications. Finally, I really want to go after the OSCP certification but I have a lot to learn before I can even attempt that. This should keep me busy for the next year to 18 months I would think. There is so much to learn and I can't wait to keep trucking along…..
Tuesday, September 11, 2012
NTFS Alternate Data Streams
While I was reading Counter Hack Reloaded I was somewhat "floored" when I got to the section about information hiding. I've worked with Windows in an enterprise environment for the last 12 years and I have never heard of NTFS Alternate Data Streams. I had no idea that it existed in NTFS and especially the way it can be used to hide data. As the wiki says, ADS allows more than one data stream to be associated with a filename using the format "filename:streamname". This information isn't listed in Windows Explorer and the stream's size isn't included in the file's size.
I'm going to try and go through some steps on using ADS to hide information.
First, I will create a text file named "host.txt" with some information in it using the following command:
echo "Stuff" > host.txt

Now I will create another text file named "evil.txt" that contains the data that I want to hide:
Echo "Evil Stuff" > evil.txt

Ok so now we have 2 files, one just normal and the other one theoretically has some bad stuff in it.
Now if you execute "type host.txt" or "type evil.txt" you can see that text appended to the end of each file.
Let's hide evil.txt in a stream in host.txt now.
type evil.txt > host.txt:evil.txt
The command executes and it looks like nothing has changed. Except for the date modified.

Now let's delete evil.txt just for good measure.
del evil.txt
Now let's see if we can view the evil.txt contents that is hidden in a stream in host.txt
more < host.txt:evil.txt

There it is, nice and hidden.
Ok so that is hiding text data, what about executables? Can you put an executable in an alternative stream and execute that? Let's try.
Let's compile a simple little C program named ads.exe to execute.
#include <stdio.h>
int main(void)
{
printf("Bad stuff just happened\n");
system("pause");
return 0;
}
The simple output is:

Now let's hide that in the host.txt file
type ads.exe > host.txt:ads.exe
Once again, nothing looks like it has changed with the host.txt file.
Now delete ads.exe
Del ads.exe
Let's try to execute the ads.exe stream.
start .\host.exe:ads.exe


I am unable to get this to execute on Windows 7 using the 'start' command. Let's try using the 'wmic' command to start a process.
wmic process call create d:\ads\host.txt:ads.exe
PERFECT!

Let's try on an XP box I have using the 'start' command.
BINGO!!

No that we've see how alternate data streams can be created, let's quickly look at a program that can be used to detect these streams.
There are quite a few out on the Internet but the one we will look at is Streams from Microsoft. You can download it and unzip it into a directory.
Doing a quick:
Streams /?
Shows a pretty simple syntax. I'll run it on the host.txt file to see what it shows.
Streams host.txt

This has 3 streams attached to it: ads.exe, ads.ps1, and evil.txt. The ads.ps1 was just something I toyed around with Powershell, you can ignore it.
This is just a quick sampling of what Alternate Data Streams are, how to create them, and just one application out there that can be used to detect. I have found these streams to be very interesting and is definitely something I will keep an eye on and do a little more research into.
Until next time….See Ya!
I'm going to try and go through some steps on using ADS to hide information.
First, I will create a text file named "host.txt" with some information in it using the following command:
echo "Stuff" > host.txt
Now I will create another text file named "evil.txt" that contains the data that I want to hide:
Echo "Evil Stuff" > evil.txt

Ok so now we have 2 files, one just normal and the other one theoretically has some bad stuff in it.
Now if you execute "type host.txt" or "type evil.txt" you can see that text appended to the end of each file.
Let's hide evil.txt in a stream in host.txt now.
type evil.txt > host.txt:evil.txt
The command executes and it looks like nothing has changed. Except for the date modified.

Now let's delete evil.txt just for good measure.
del evil.txt
Now let's see if we can view the evil.txt contents that is hidden in a stream in host.txt
more < host.txt:evil.txt

There it is, nice and hidden.
Ok so that is hiding text data, what about executables? Can you put an executable in an alternative stream and execute that? Let's try.
Let's compile a simple little C program named ads.exe to execute.
#include <stdio.h>
int main(void)
{
printf("Bad stuff just happened\n");
system("pause");
return 0;
}
The simple output is:

Now let's hide that in the host.txt file
type ads.exe > host.txt:ads.exe
Once again, nothing looks like it has changed with the host.txt file.
Now delete ads.exe
Del ads.exe
Let's try to execute the ads.exe stream.
start .\host.exe:ads.exe


I am unable to get this to execute on Windows 7 using the 'start' command. Let's try using the 'wmic' command to start a process.
wmic process call create d:\ads\host.txt:ads.exe
PERFECT!

Let's try on an XP box I have using the 'start' command.
BINGO!!

No that we've see how alternate data streams can be created, let's quickly look at a program that can be used to detect these streams.
There are quite a few out on the Internet but the one we will look at is Streams from Microsoft. You can download it and unzip it into a directory.
Doing a quick:
Streams /?
Shows a pretty simple syntax. I'll run it on the host.txt file to see what it shows.
Streams host.txt

This has 3 streams attached to it: ads.exe, ads.ps1, and evil.txt. The ads.ps1 was just something I toyed around with Powershell, you can ignore it.
This is just a quick sampling of what Alternate Data Streams are, how to create them, and just one application out there that can be used to detect. I have found these streams to be very interesting and is definitely something I will keep an eye on and do a little more research into.
Until next time….See Ya!
Subscribe to:
Comments (Atom)
